Trustwave DbProtect
Database activity monitoring (DAM) and vulnerability assessment.
Databases are a prime target for attackers due to the amount of sensitive information they store such as customer information, intellectual property and proprietary secrets. Yet many businesses fall victim to database intrusions because of common flaws. Trustwave DbProtect is database security software that helps businesses prevent database breaches with database activity monitoring (DAM) and vulnerability assessment.
Along with DAM, DbProtect can perform blocking, locking and termination functions when malicious activity is detected. DbProtect’s assessment capabilities include identifying database vulnerabilities, configuration errors, rogue installations, and access issues.
Overview:
Trustwave DbProtect is a security platform designed for consistent monitoring and management of enterprise databases within the data center.
Built on a centrally managed and distributed architecture, DbProtect uncovers database weaknesses. This includes configuration mistakes, identification and access control issues, missing patches, or any toxic combination of settings that could lead to escalation of privileges attacks, data leakage, denial-of-service (DoS), or unauthorized modification of data held within data stores – both relational databases and big data stores.
Through its multi-user/role-based access, distributed architecture and enterprise-level analytics and reporting, DbProtect enables organizations to secure all of their relational databases and big data stores throughout their environment (on premise or in the cloud) and achieve business objectives.
The quality of a database security solution directly correlates with the quality of its checks and tests. And a set of tests and checks is only as good as the research team that keeps it current. Trustwave SpiderLabs® is the leading database vulnerability research team in the industry and discovered 80 percent of the database vulnerabilities patched over the past four years. Our experts have discovered and reported hundreds of vulnerabilities in Oracle databases and dozens in Microsoft SQL Server, IBM DB2, MySQL, Sybase ASE and Hadoop.
Why do our customers choose DbProtect for their enterprise database security needs?
Complete, Accurate and Intuitive
Discover new or rogue installations, develop security policies, perform safe penetration tests, audit for policy violations and deliver comprehensive reports on the security of your data stores from every possible angle.
Configurable Policies
Create policies ranging from all-encompassing to customized, depending on the specific needs of a business unit or workgroup. Multiple policies can be used to accommodate an organization's various business, security and compliance needs.
Soup-to-Nuts Remediation Guidance
Facilitates delegating efforts to address open issues, policy violations or vulnerabilities across your organization. Then, automatically forwards reports to respective administrators for immediate action.
Compatible and Complementary
Easily layer DbProtect into your existing security management, risk mitigation and compliance efforts.
Distributed Architecture
Meets the scalability demands of large organizations with thousands of data stores. Distributed management and scheduling features enable an enterprise to assign and schedule remote engines to scan, and pull those results back to a central management console for analysis. The web-based user interface is designed for multi-tenancy and ensures database reviews are segmented.
Comprehensive Reporting
Able to produce hundreds of reports for all levels of the organization. Reports offer different level of summary and detail depending on the audience level – and can include compliance, security, trend (risk calculation over time) and operational (inventory of databases and their populations) information.
Database Activity Monitoring
Identifies and alerts on unusual or suspicious behavior to help correlate with other network events.
Data Security Knowledge Base
Acquire extensive and continuously updated analytics of relational databases and big data security best practices, configuration settings and vulnerabilities.
Supported Database Types
- Microsoft SQL Server
- Microsoft SQL Azure
- ORACLE
- SYBASE
- MySQL
- IBM|DB2
- hadoop
Features:

Discover
Review: Seamlessly survey your environment's accessible assets, user access levels and security feature usage.
Inventory: Identify and highlight recently added, rogue or missing data store installations and objections.
Verification: Quickly ascertain the configuration state of all of your data stores (relational or big data).

Assess and Monitor
Flexibility: Obtain an agentless assessment approach with no impact on the target data store.
Reference Center: Access a comprehensive and continuously updated library of relational database and big data store vulnerability and security configuration issues – backed by our elite SpiderLabs research team.
Activity Monitoring: Maximize the depth and breadth of intrusion detection and activity auditing through a hybrid architecture that examines any access to confidential information in your database.

Report
Visibility: Gain a consolidated view of vulnerabilities, threats, risks and compliance efforts across varied data store environments – through reports and dashboards.
Empowerment: Enables users to document their current status, and demonstrate progress, effectiveness and operational efficiency.
Granular: Evaluate trends and drill down for a comprehensive view of each individual database or group of databases.
How It Works:
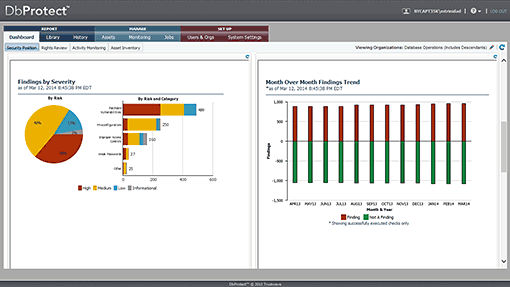
One of the main dashboards for vulnerability scanning chronicles findings by risk and illustrates them through trending graphs.
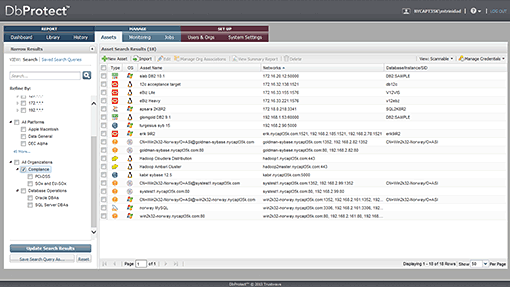
The DbProtect Asset Management system allows users to access to the databases they only need to see. A role-based access control component ensures different access depending on one’s role.
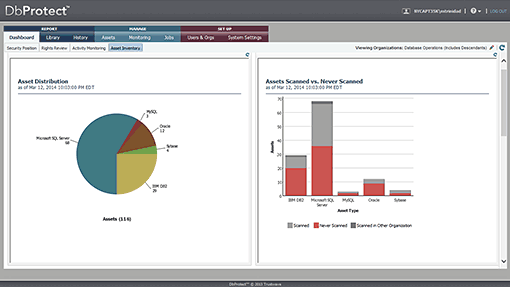
The Asset Inventory dashboard allows users to see all the databases within their organizational view. They can track which assets are scanned versus not scanned, as well as the breakdown of asset types discovered on their network segmentation.
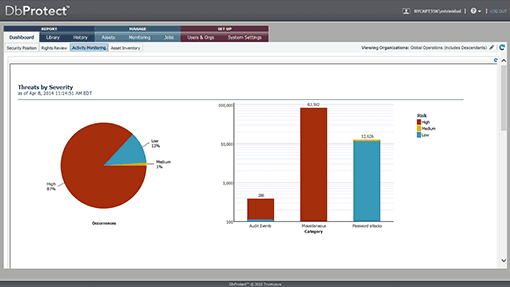
An easy-to-decipher dashboard presents real-time activity analysis that maximizes protection and limits false positives.
Documentation:
Download the Trustwave DbProtect Datasheet (PDF).
Download the Trustwave Database Risk Assessment Service Datasheet (PDF).
