Trustwave Two Factor Authentication
Built-in threat intelligence, a unique combination of positive and negative security,
The corporate perimeter has changed; users no longer access applications and data from their corporate network alone. Company resources are accessed with smartphones, tablets and other on-the-go devices. In addition, many businesses are required to employ authentication solutions, as mandated by the Payment Card Industry Data Security Standard (PCI DSS), FFIEC Authentication Guidance and other regulations. Yet many organizations remain dissatisfied with traditional hardware-based authentication, which can be costly and cumbersome for administrators and users alike.
Trustwave's cloud-based two-factor authentication solutions help you to secure access to networks and applications, protect users, and address compliance requirements for the protection of regulated data, while simplifying deployment and management, improving user experience, and minimizing the cost and hassle of traditional hardware tokens.
Overview:
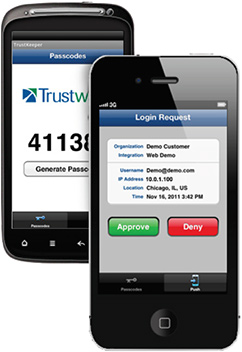
For decades, hardware-based tokens have been the standard for secure two-factor authentication. Unfortunately, these traditional solutions require a significant amount of time and cost to deploy and manage. Trustwave delivers a solution that combines flexible authentication methods, cloud-based delivery and self-service administration with seamless management. With low, per user fees, our solutions are easy to provision and inexpensive to maintain, supporting any use case including: network or application authentication from the corporate desktop, remote locations, employee laptops and mobile devices, such as smartphones and tablets.
Flexible Options — "Mix & match" authentication options support any scenario - from the corporate network to remote locations to mobile access.
Easy Management — Cloud-based self-provisioning can take place from anywhere on the network with minimal administrative support.
Lower Cost — A low, per user annual price means strong authentication at a fraction of the cost of traditional, hardware-based solutions.
Simplified Compliance — Helps you meet the access control requirements of compliance mandates including FFIEC Authentication Guidance, PCI DSS and others.
| Cost | Traditional Token Based Authentication | Trustwave Authentication Solutions | Advantages |
| Start-up Implementation | No separate hardware purchase No control software to install | ||
| User Deployment and Experience | No separate infrastructure needed Simple integration with existing VPN and Web applications | ||
| Hardware and Infrastructure | Not Applicable | No separate infrastructure needed Simple integration with existing VPN and Web applications | |
| On-going Maintenance and Support |
|
Features:
Traditional authentication practices that depend on hardware tokens are especially complex and costly for a growing organization. Trustwave helps you secure access to your systems and protect your users while reducing cost and improving management. And our flexible solution can easily scale to meet your demands as your business grows.
Multiple AuthenticatorsUsers are given a choice of device and authentication method each time they log in. We allow for choice and flexibility, creating an authentication solution that works for everyone in your organization. And Trustwave supports all phone types — from smart phones (on all platforms) to landlines — and lets users authenticate using any of the following:
- Push — Push notification for login request approval/denial
- Mobile — One-time passcode generation via mobile application
- Voice callback — Push button authentication
- SMS — One-time passcode sent via SMS text
- Digital certificates — Trustwave-issued user authentication certificates
Clearly showing the authentication process reduces user confusion and corresponding support desk call volume. Users get confused and worried when a page appears to “hang” and stop responding during login. Trustwave provides live-updating status messages to show users the authentication status or report any errors.
Powerful ManagementOur intuitive Web portal allows your administrators to easily enroll and revoke access your mobile and remote workforce almost instantaneously. Administrators can automatically lock out users after a specified number of invalid logins, and get real-time fraud alerts when users report potentially fraudulent logins. In addition, the administrative interface also allows for customization of the service: everything from voice prompts to caller ID to SMS batch sizes and expiration can be customized for your organization.
How it Works:
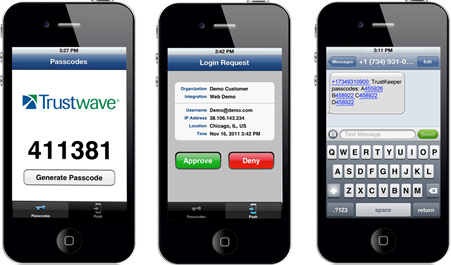
Trustwave two-factor authentication leverages your current VPN authentication infrastructure, including your corporate directory system and VPN hardware, and can be implemented and operational with just four easy steps:
- You deploy a trusted root certificate to your VPN hardware devices to provide a point from which administrators can control user access.
- Network administrators log into the co-branded Trustwave management portal to provision certificates for employees and contractors.
- Users access a simple co-branded Web portal to set a certificate password, download the certificate and install it on their remote system.
- When a user logs into the VPN, they are prompted to use the certificate and password for authentication.
Documentation:
Download the Trustwave Two Factor Authentication Datasheet (PDF).
