FISMA Compliance
The Federal Information Security Management Act of 2002, or FISMA, requires the protection of data that is created, stored or accessed by the federal government. Specifically, federal agencies must create an information security program made up of eight components. In addition, each agency must annually report its progress to the Office of Management and Budget. This information is used to make an annual report to Congress on FISMA implementation across the executive branch.

49%
of breaches at federal agencies are caused by employees not complying with security policies

36 MILLION
Social Security numbers were involved in a recent government breach

23 OF 24
federal agencies had weaknesses in computer access controls, according to the GAO
Overview:

Federal government agencies must comply with FISMA, but the law has been expanded to include others as well: state government agencies that administer federal programs, in addition to private vendors that maintain contracts with the federal government. However, those non-federal organizations do not have to validate compliance.
According to FISMA, a comprehensive information security program should include the following:
- Establish a program for managing information security risk
- Document policies and procedures
- Select security controls for systems
- Establish a security training program
- Monitor controls on an ongoing basis
- Establish a remediation program
- Establish an incident response and reporting program
- Establish a continuity-of-operations balance
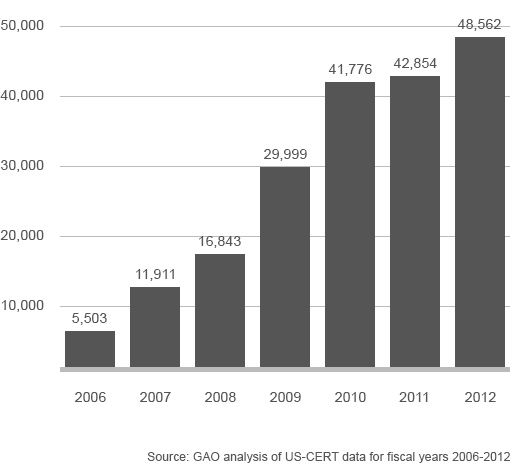
Data Breaches Reported by Federal Agencies 2006-2012
FISMA also requires the National Institute of Standards and Technology (NIST) to create guidelines and standards that agencies use to protect their information assets. A recent revision to NIST’s SP 800 series of computer security publications, which assists agencies in their FISMA compliance through a risk-based approach, includes an increased focus on the insider threat, mobile devices, advanced persistent threats and supply-chain risk.
There also is increased emphasis on continuous monitoring. To validate compliance, the chief information officers of federal agencies are required to submit monthly data feeds from their automated security management tools into CyberScope, a web-based reporting tool released by the Office of Management and Budget. Inspectors general for each agency also are required to make an annual report through CyberScope.
The Department of Homeland Security (DHS) then assesses the CyberScope data and asks agencies to develop a plan-of-action to remedy any shortcomings. In addition, DHS conducts annual interviews with the CIOs and CISOs of each agency to determine their progress toward security best practices and FISMA compliance.
In 2011, the U.S. Government Accountability Office (GAO) found that data breaches at federal agencies rose 650 percent in five years. Along the way, the GAO, which is the independent investigatory arm of Congress, has audited numerous agencies, often resulting in findings of lax security. The GAO’s reports are made public and typically attract widespread press coverage. In its reports, the GAO has discovered the implementation of weak security controls, mostly around data/device protection, access limitations, patch management awareness training and risk assessments. A recent review by the GAO found that the 24 major federal agencies have achieved many of the pieces required for a successful information security program, but there are still improvements to be made.
Consequences:
There is no formal penalty structure for non-compliance, although legislation has circulated that would create that. However, agencies face reputational harm for failing to comply because an annual FISMA report is presented to Congress. In addition, agencies failing to comply face the possibility of budget cuts. As well, their information and security leaders may be forced to testify before federal lawmakers to explain their poor security posture.
Solutions:
Through a comprehensive portfolio designed to respond to modern-day security threats, Trustwave helps government agencies ensure compliance with FISMA requirements.
Plan and Prepare
Conducting a Risk Assessment is the first step to identifying and implementing safeguards necessary to meet compliance. Trustwave helps you find gaps that may exist between your current security posture and FISMA requirements. The customizable assessments, scaled individually for your government agency, include identification of key assets and IT systems, assessment of controls and frameworks and a review of third-party providers and incident response programs.
Address Gaps and Vulnerabilities
FISMA requires government agencies to establish a comprehensive information security program. Here are some of the ways we can help:
SIEM
Helps you gain broad visibility of threats to your network and improve your compliance process through logging, monitoring, and analysis of events.
Network Access Control
Ensures managed and unmanaged devices connecting to the network comply with policies and do not introduce malware.
Data Loss Prevention
Allows you to discover and classify sensitive data and prevent it from leaving the network.
Web Application Firewall
Protects web applications against external attackers who may use vulnerabilities, such as SQL injection, to steal sensitive data.
Secure Web Gateway
Prevents bandwidth-hogging spam and data-stealing attacks from entering the network, while inspecting outbound content to ensure confidential data doesn’t exit.
Incident Readiness and Response
Prepares your staff to proactively identify the indications of a breach and contain it quickly and effectively.
Security Awareness Education
Instructs your employees and contractors to understand the threat of social engineering and follow best practices for security, including password management and the safe use of web and social media tools.
Automate and Manage Compliance
TrustKeeper Compliance Manager helps you to centrally automate and manage controls, policies and procedures across multiple compliance frameworks, including FISMA. Compliance Manager is delivered through our cloud-based management portal TrustKeeper, which provides a real-time view into the status of your compliance and security programs and offers access to all of your managed services. Through one easy-to-use dashboard, you can submit support requests, see event history, run reports and manage your account at any time.
Documentation:
Download the Trustwave Security Solutions for Government Data Sheet (PDF).
