Trustwave Vulnerability Management
Identify Vulnerabilities Before an Attacker Does
Keep track of the systems, applications and databases on your network – and their associated vulnerabilities – throughout their lifecycle and evolution. Trustwave Vulnerability Management offers you a front-row view into the systems, applications and databases residing on your network and how those assets may be vulnerable to attack.
Overview:
Trustwave Vulnerability Management allows you to manage a prioritized list of vulnerabilities, understand how to fix them and produce reports detailing and verifying your remediation progress over time. Why do businesses choose Trustwave over the competition for vulnerability scanning and management?
- Application of threat data from Trustwave SpiderLabs’ industry-leading research
- Significantly fewer false positives and increased scan efficiency
- Centralization of both internal and external scanning management
- Integration with a number of Trustwave products and services including, Compliance Manager and Unified Threat Management (UTM)
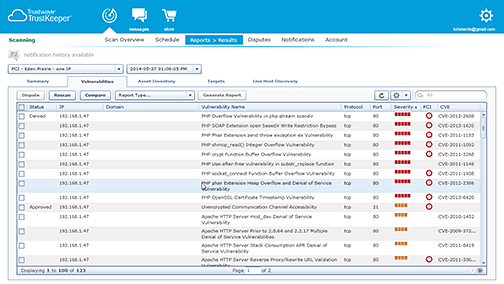
Features:
Context-driven Scanning
Using OS, protocol and application fingerprinting and other gathered knowledge to target vulnerabilities directly, Trustwave Vulnerability Manager significantly reduces false positives, decreases the time it takes for a scan to complete and allows for the effective assessment of applications with non-default installations.
Powered by Trustwave SpiderLabs
To protect against next-generation threats, our scanning technology applies threat data gleaned from Trustwave SpiderLabs experts’ proprietary research, including incident response and forensics cases, penetration testing and malware analysis.
Flexible, Continual Scanning
Scans can be run ad-hoc or at regular intervals to identify new risks across the network. Configurable notifications keep you up to date on upcoming scans, scan kick-offs, scan completion and vulnerability dispute status (in bulk or otherwise).
IT Asset Change Control
Compare easily generated reports to detect when a system or network service is added or removed from the environment. Correlate results for tracking of vulnerability trends and asset changes over time to measure the effectiveness of IT remediation processes.
Proprietary Research and Development
Tests and plug-ins written by our dedicated vulnerability scanning research team keep you up to date on emerging threats, reduce false positives and result in more accurate findings.
Risk Assessment
Integration with other Trustwave services provides a complete view of vulnerability risk exposure across the organization.
Benefits:
Trustwave Vulnerability Manager, housed within the award-winning TrustKeeper portal, provides IT and security professionals with insight into their network vulnerabilities and exposure to attack and/or compromise from outside and inside the corporate firewall
Trustwave Vulnerability Manager helps customers meet both IT security objectives – such as protecting confidential data and ensuring the integrity and availability of IT systems – and compliance goals, including auditing security controls to safeguard sensitive information.
Trustwave Vulnerability Manager centralizes the management of these processes in the cloud to allow customers to:
- Demonstrate compliance via audit-ready reporting
- Stay protected from emerging threats
- Scan continually to gain real-time insight
- Monitor networks to understand IT inventory
- Take immediate action on discovered vulnerabilities with recommendations from Trustwave security experts
How It Works:
You begin managing the vulnerabilities within your network by logging into the portal to schedule an internal or external scan.
Your scan will begin on the date you select and proceed to execute the following progression:
- System Discovery
Identifies servers, appliances and other devices on the network. - Service Discovery
Identifies the open ports and services available on each discovered system, such as mail and web servers. - Vulnerability Detection
Performs tests based on the OS, protocol and application fingerprinting data gathered in the discovery phase. - Vulnerability Classification
Scores, ranks and identifies vulnerabilities using the Common Vulnerabilities and Exposures (CVE) dictionary and Common Vulnerability Scoring System (CVSS), industry standards for tracking and calculating vulnerability risks. - Reporting
Gathers findings within the portal and prioritizes and organizes them according to your preferences. - Management
Sort and track vulnerabilities based on asset class for remediation to make risk reduction efforts actionable.
